In the modern era of software development, the management of environment variables and secrets is paramount to ensuring the security and integrity of applications. However, the conventional practice of storing sensitive information in .env files poses significant risks to data security and can lead to severe consequences if not handled with care.
Why .env Files Are Dangerous
Traditionally, .env files have been used to store environment variables, including sensitive information such as API keys, database credentials, and authentication tokens. While this method offers convenience and simplicity, it comes with inherent security vulnerabilities that can be exploited by malicious actors.
One of the primary concerns with .env files is their susceptibility to exposure. These files are often included in source code repositories, making them accessible to anyone with access to the codebase. Inadvertent exposure of .env files can occur through misconfigurations, insecure storage practices, or unauthorized access to version control systems.
Furthermore, .env files lack encryption, leaving sensitive data in plaintext. This makes it easy for attackers to intercept and exploit these credentials, potentially leading to data breaches, financial loss, or reputational damage for organizations.
The Importance of Incorporating Advanced Security Features
To mitigate the risks associated with storing environment secrets in .env files, it's essential to incorporate advanced security features into the development workflow. Here are some crucial features, which come pre-packed into platforms like envsecrets.com, that can enhance the security posture of applications:
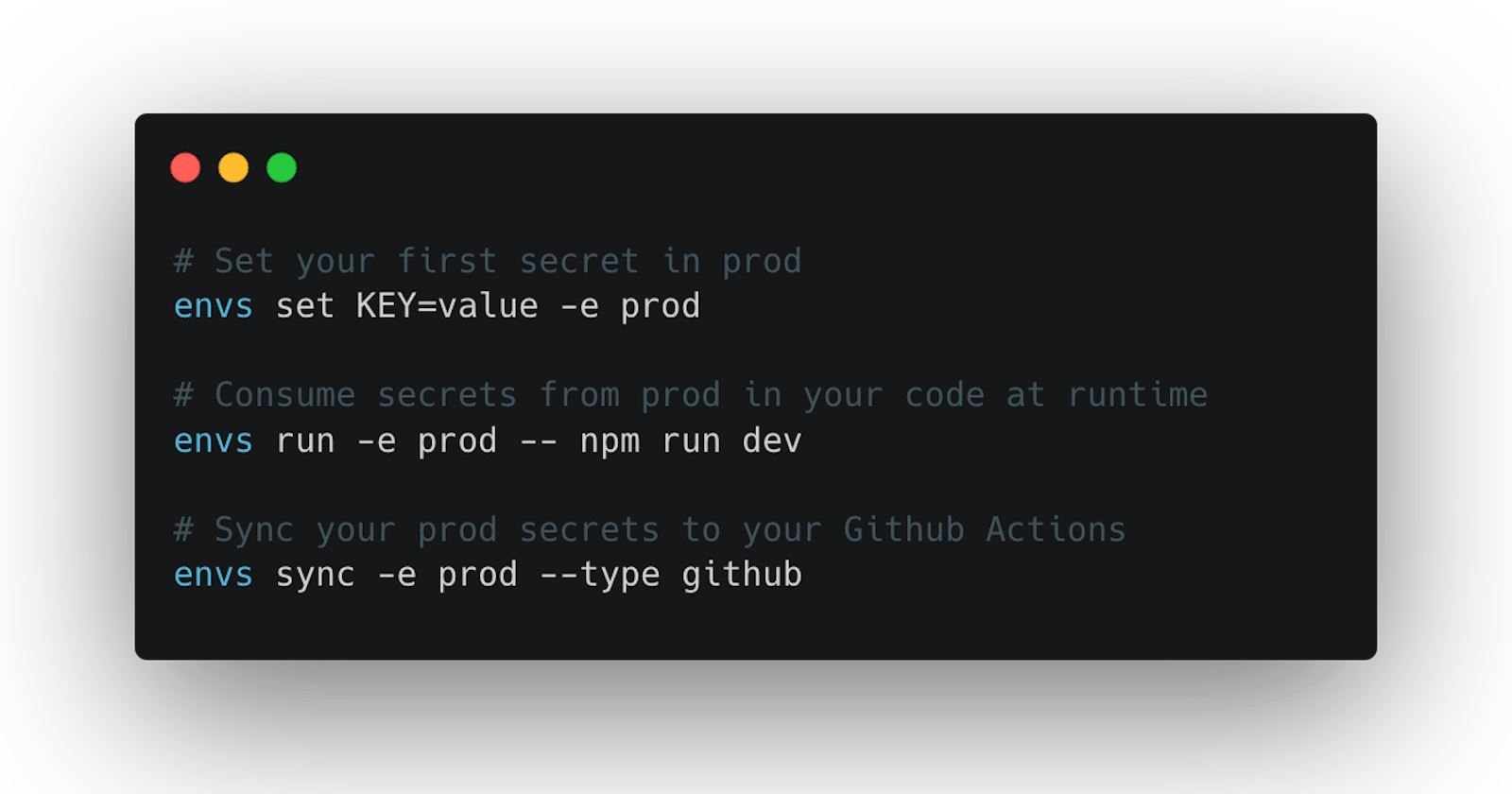
1. CLI First Control of Your Secrets
Implementing a command-line interface (CLI) for managing secrets allows developers to securely store, retrieve, and manipulate sensitive information without exposing it in plaintext. CLI-first platforms, like envsecrets.com, offer encryption capabilities, access controls, and audit trails, providing a robust solution for secret management.
2. Role-Based Access Control
Role-based access control (RBAC) enables organizations to enforce granular permissions and restrictions based on user roles and responsibilities. By implementing RBAC, organizations can ensure that only authorized individuals have access to sensitive information, reducing the risk of insider threats and unauthorized access. For example, envsecrets.com comes with inbuilt RBAC support.
3. Deployment Platform Integrations
Integrating secret management solutions with deployment platforms such as Vercel and Docker enables seamless provisioning and deployment of applications while ensuring the protection of sensitive data. These integrations automate the process of securely injecting secrets into application environments, eliminating manual intervention and reducing the risk of human error.
4. Versioning
Versioning of secrets allows organizations to track changes, revert to previous states, and maintain an audit trail of access and modifications. By implementing versioning, organizations can enhance accountability, transparency, and traceability in secret management practices.
5. Multi-Factor Authentication
Enforcing multi-factor authentication (MFA) adds an extra layer of security to the secret management process by requiring users to provide multiple forms of verification before accessing sensitive information. MFA mitigates the risk of unauthorized access due to stolen credentials or compromised accounts, enhancing overall security posture.
6. Third-Party Synchronization
Pushing secrets to third-party services such as Github Actions, Vercel, Railway, and ASM facilitates seamless integration with external workflows and environments. By synchronizing secrets across platforms, organizations can ensure consistency, compatibility, and security across their entire ecosystem. One of the best platforms that handles third-party integrations natively with multiple platforms is envsecrets.com.
In conclusion, while .env files have been a common method for storing environment secrets, they pose significant security risks that must be addressed. By incorporating advanced security features such as CLI first control, RBAC, deployment platform integrations, versioning, MFA, and third-party synchronization, organizations can enhance the security and integrity of their applications while safeguarding sensitive information from potential threats.